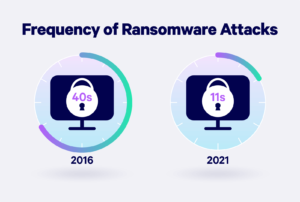
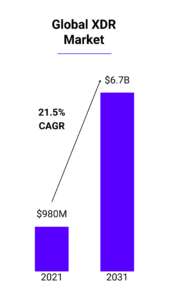
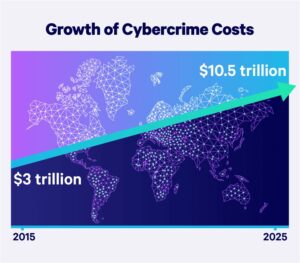
Meanwhile, organizations are fighting their own challenges based on several industry trends, including:
- Small and medium-sized enterprises (SMEs) are continually under threat, with 46% of cyber attacks targeting businesses with fewer than 1000 employees.
- Cybersecurity talent is nearly impossible to recruit and retain, and over 70% of short-staffed organizations believe their lack of coverage puts them at significant risk.
- Disparate cybersecurity tools continue to speak different languages, which makes analysis—correlating data and creating context-driving insights—time-consuming, costly and at times, impossible.
- The cost of data ingestion continues to escalate; current subscription models haven’t kept up with mixed environments of cloud and on-premise, squeezing budgets and forcing security leaders to make difficult tradeoffs.
How do you protect your enterprise with little manpower, deflating resources, and a market of alphabet soup products? The global cybersecurity workforce gap grew 350% between 2013 to 2021, from 1 million to 3.5 million jobs unfilled. If this gap is any indicator, these challenges will continue to worsen. Only heightening our concerns is the fact that we are outnumbered. A recent report highlighted that according to the FBI director, Chinese hackers outnumber FBI cyber staff 50 to 1.
In our view, these inefficiencies are driving up cybersecurity spend awhile keeping security teams in a defensive mode, constantly reacting to threats. Tomorrow’s XDR will fully enable security teams to shift into a proactive strategy, while driving overall efficiencies and improved outcomes.
Technology Innovation and the Promise of XDR
Lately, Extended Detection and Response (XDR) has shown promise in helping businesses overcome these challenges—but we believe that today’s solutions have not yet achieved the promise of XDR. To overcome our industry’s biggest hurdles, we propose tomorrow’s XDR: a data-agnostic and outcomes-driven approach for security correlation, where data is automatically ingested, modified, and processed from source to correlation—removing the over-reliance on expert users as part of what is currently a noisy, complex, and highly manual process.
The goal of tomorrow’s XDR is security correlation, not aggregation. Even if you have all the data at your fingertips, security teams can’t protect what they an ecosystem of solutions. can’t see or know to find. Instead of dumping data into a centralized location (e.g., SIEM) and relying on experts to create complex rules, tomorrow’s XDR will perform data hygiene at speed and scale, working out complex data manipulations earlier so that IT managers and
others who protect the enterprise can proactively detect threats, respond to them, and remediate issues through a simple and easy-to-use interface. To do this effectively, XDR will rely on
With the global XDR market predicted to grow from nearly $1 Billion to $7 Billion in the next 10 years, it is currently being viewed as the crucial next step in adding automation, efficiency, and visibility that organizations need to keep up with broadly experienced challenges, but why? To explore this answer, we start with a brief history of how we got here, and how the lessons and complications from our industry’s past inform the requirements of the XDR of tomorrow.
How we got to where we are today
When the internet was born, malware started off as a series of simple pranks. These pranks quickly evolved into methods of destruction, through rewriting data on disks or blocking systems from use (i.e., denial-of-service attacks). Technology providers rose to the challenge of defending against these threats, focusing on protecting the endpoint—any physical device used to connect to a network, such as a phone, laptop, desktop, or server.
AV: detect known signatures
The first product for endpoint production was antivirus (AV) software in the 1980s. AV detects malware through known signatures—unique patterns of binary code—present in the malware’s software. AV still serves a role today as the first layer of defense, for scanning files and network traffic to detect known malware.
Signature: a unique pattern of binary code that is used to identify malware
However, cybercriminals easily evade known signatures by changing a small bit of code while still maintaining the code’s original intent; now the signature no longer matches, and the AV no longer catches it. As a result, AV left a large gap: how do we detect malware before we know it exists? How do we minimize the mean time to identify a threat, and thus minimize or prevent the damage?
According to IBM’s Cost of a Data Breach Report 2022, the average time to identify and contain a breach is 323 days, which drops to an average of 249 days with fully deployed automation. This difference in time translates to a significant difference in the cost of damages—as the report found, from an average of $6 million to $3 million.
EDR: identify suspicious behavior
The answer to minimizing this gap is to identify suspicious behavior (i.e., unknown malware) vs. just the presence of known malware. Enter endpoint detection and response (EDR). Developed in the early 2010s, EDR automatically monitors suspicious behavior like injection of code into another process, or exfiltration of data with unusual network protocols. Most EDRs also package themselves with AV to catch known signatures, but the EDR function itself is separate from AV.
The first iteration of EDR looked at individual endpoints but didn’t compare them against each other. If one was compromised by a zero-day attack, you couldn’t use the software to compare or push warnings to the others; each endpoint was essentially independent.
Zero-day attack: an attack that takes advantage of a vulnerability that is unknown to the public and therefore has no patch
The second iteration—what EDR is today—manages and compares all endpoints as one collective. You can receive an alert of a zero-day attack on one endpoint, catalog and push a signature to all other endpoints, and detect if an attacker is making lateral a movement—hopping from one computer to the next—to find high-value assets on your network.
Lateral movement: when an attacker moves from one system to another, typically to find high-value assets or their ultimate target
While EDR is a significant advancement from AV, it only catches subsets of attacks due to the ever-changing nature of cyberspace. At constant war, attackers are always looking for ways to evade EDR, and are often successful. In a recent paper in the Journey of Cybersecurity and Privacy, researchers simulated four representative attack vectors, which none of the leading EDR solutions were able to detect and prevent. If EDRs are unable to detect attacks, at a minimum they should log behavior, but as the researchers found, many do not.
SIEM: a single pane of glass
With EDR catching and mitigating only a subset of attacks, logging events became a necessity to compile data from which expert cybersecurity analysts could dig in to detect an attack—an improvement over the capabilities of EDR alone.
To effectively track and assess a threat, analysts need to be able to find and cross-correlate data from multiple, disparate sources. This is the gap that a security information and event management (SIEM) tool addresses. First introduced to the market in 2005, a SIEM ingests data from the EDR and other sources (e.g., firewall, network devices, Active Directory) onto a centralized platform for enterprise-wide visibility. With a SIEM, analysts can correlate security events, set alerts, and respond to incidents in real-time.
With all the promise SIEM holds, it comes at an increasingly unaffordable cost, both in pricing and staffing. SIEM vendors quote subscription models based on the volume of data ingested; with mixed environments such as cloud and on-premise, this cost has increased exponentially – with no end in sight. The requirement to pay for data twice, both retained in the cloud and in the SIEM, for example, is driving costs that are significantly out of line with today’s budgets. SIEM technology also requires expert cybersecurity professionals familiar with the tool to make it effective, which has become next to impossible today – even for those businesses that can afford to hire and retain the talent when they find the right candidates.
The rise of the SOC
AV is simple: set it and forget it, but it’s only as good as its database of signatures. EDR took defense a step further by identifying suspicious behavior across multiple endpoints. SIEM technology now fulfilled the need to log and centralize data beyond what EDR is able to capture. This evolution beyond AV created a new set of requirements: security professionals who know what they’re looking at and how to respond—across multiple vendors, technologies, and application languages.
The team of security professionals who secure your enterprise, along with the infrastructure of specialized technology, forms your security operations center (SOC). To identify potential threats, SOC analysts use indicators of compromise (IOCs)—information that indicates malware or that an attacker might be present on the network. A SOC analyst maps IOCs to alerts, tracks an attacker’s activity, and responds to the threat while ensuring business operations sustain.
Indicators of compromise (IOCs): information that indicates the potential presence of malware or an attacker on the network. Typical IOCs include files, IP addresses, and URLs.
With the sheer volume of data and alerts coming into a SIEM daily, SOC teams must sift through false positives and fine-tune the SIEM to their corporate environment. Burnout is a serious problem: in a recent global survey, over half of respondents received 500+ alerts a day, missed critical alerts daily or weekly, and cited alert fatigue as a key reason for turnover.
Many organizations struggle to find competent professionals to protect their enterprise—that’s where Managed Detection and Response (MDR) comes in.
MDR: Human-led, comprehensive security operations capabilities
If you’re lacking a SOC or seeking support for your current one, Managed Detection and Response (MDR) offers SOC-as-a-service with EDR. With MDR, you’re paying for access to a dedicated team of SOC analysts 24/7 who will monitor, investigate, and respond to alerts triggered in your EDR and more. The availability of MDR made it possible for SMEs to benefit from the talent and scale of enterprise-grade security operations solutions.
Depending on the tier of service, Your SOC team will staff security analysts that monitor alerts and decide those that require escalation, respond to incidents to investigate the damage done and clean an infected machine, and proactively search through logs and data to find threats that your EDR has not yet identified.
The beauty of MDR lies in lifting the burden of infrastructure and staffing to a specialized third-party that can recruit, retain, manage, and train SOC teams and talent – all while managing your security operations around the clock.
MSSP, MSP, MDR: everyone’s an MDR
If you seek a service like MDR, there are 1000s of different types of providers from which to choose. According to a February 2023 Gartner® Report, Managed Detection and Response (MDR) services provide customers with remotely delivered security operations center (SOC) functions. These functions allow organizations to rapidly detect, analyze, investigate and actively respond through threat disruption and containment. They offer a turnkey experience, using a predefined technology stack that commonly covers endpoint, network, logs and cloud. According to Gartner® in the same report, core capabilities include:
- 24/7 remotely delivered detection and response functions.
- A provider-operated technology stack that enables and coordinates real-time threat detection, investigation, and active mitigating response.
- Whether it is developed by the MDR provider, an integrated set of commercial technologies that use modern techniques (like APIs) to exchange data and instructions, or a combination of both approaches.
- Staff that engage daily with individual customer data and have skills and expertise in threat monitoring, detection and hunting, threat intelligence (TI) and incident response.
- Turnkey delivery, with predefined and pre-tuned processes and detection content. This includes a standard playbook of workflows, procedures and analytics, and requires a minimum viable set of telemetry to deliver services; offering integration with third-party detection and response technologies beyond provider-owned technologies.
- The availability of immediate remote mitigative response, investigation and containment activities (such as quarantining hosts and de-authenticating users) beyond alerting and notification, delivered and coordinated by service provider staff.
- Triage, investigate and manage responses to all discovered threats, regardless of priority with no limitations on volumes or time dedicated to the discovery and investigation process.
The above offers a brief overview of Gartner® MDR requirements. If you would like to learn more, download a complimentary copy of the report at https://info.cybersainik.com/gartner-market-guide-mdr.
A managed services provider (MSP), a traditional managed IT service, will now offer MDR services as an added service. A managed security service provider (MSSP), which inherently focuses on security, offers MDR as part of its standard services. Traditionally EDR vendors also want in; they’ve acquired companies with SIEM capabilities, and while you can still buy EDR on its own, they will also offer MDR.
MDR has gained significant traction, with a market growth of nearly 49% compared to the rest of the managed security services market growing at roughly 9%. With results such as 50% less time to detect a threat and 50% reduction in cost savings, this is no surprise. Organizations are moving to outsourced SOCs because building and maintaining these capabilities in-house has proven to be unsustainable or sometimes unachievable (costing over $1million JUST to stand up). In fact, Gartner® also noted in a 2021 SOC report, “By 2025, 33% of organizations that currently have internal security functions will attempt and fail to build an effective internal SOC due to resource constraints, such as lack of budget, expertise, and staffing.”
The cloud changes the game
Industry players have jumped on the SOC + SIEM bandwagon as MDR providers, as data ingestion is where the money is made. The prominence of cloud, however, has made this model unsustainable. The cost of data silos becomes hard to ignore; are you supposed to ingest all cloud data into an on-premise solution? Or ingest all on-premise data into the cloud? Either way, you are required to pay for data at least twice.
Take it from Rob Anderson, one of Cyber Sainik’s Advisory Board members: “After 40 years in cybersecurity, collaborating with CISOs across organizations of all sizes, a common frustration I hear is the exponential cost of re-ingestion. If you have data sitting in AWS, Azure, and your EDR, you have to re-ingest data from all three sources back to your on-prem SIEM. You will pay for that data multiple times, which is unacceptable.”
So the challenge is: how do you ingest, correlate and utilize the necessary data elements across multiple silos, without paying for it multiple times over?
A vision for XDR: correlation at speed and scale without storage and centralization
What if the answer to ingestion and utilization vs. storage and centralization is this: Consider the reason you needed to use data in the first place: to better find and cross-correlate data from multiple sources. What if something could do that for you—at speed and at scale—without having to centralize and store data multiple times?
Stay tuned for the second article in our series. We address our vision for Extended Detection and Response (XDR) and explore its potential impact on the challenges cybersecurity teams are facing. In an ongoing pursuit of improved outcomes, reduced costs and maximized efficiency we believe tomorrow’s XDR could hold the answer – but understanding how a modern approach should be viewed is the next critical step in helping us achieve proactive versus reactive defense strategies.
1 | Gartner®, Market Guide for Managed Detection and Response Services, Pete Shoard, Al Price, Mitchell Schneider, Craig Lawson, Andrew Davies, 14 February 2023
2 | Gartner®, SOC Model Guide FOUNDATIONAL Refreshed 5 April 2023, By John Collins, Mitchell Schneider, Pete Shoard, 19 October 2021
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.